Delhi Blast Case: What’s Real, What’s Doubtful – Full Breakdown
On a cold evening in Delhi, right outside the historic Red Fort, a blast instantly turned a calm traffic zone into chaos. A car packed with explosives detonated, sending shock and fear across the city. As the dust settled, what emerged was not just a tragic accident but the beginnings of a much deeper investigation—one that revealed a digital trail, medical professionals, encrypted servers and a possible network far more organised than anyone expected.
Three doctors from Al Falah University—Umar Un Nabi, Muzammil Ganaie and Shaheen Shahid—quickly came under the spotlight. These were not amateurs or fringe individuals. These were young professionals, allegedly operating in an organised, methodical manner. Several major news outlets confirmed their identities and their suspected roles. It is believed that Dr Umar was driving the explosive-laden car at the time of the blast, making him a central figure in the case.
What the article claims (and seems credible)
Three suspects under investigation
- The article identifies three doctors — Dr Umar Un Nabi, Dr Muzammil Ganaie and Dr Shaheen Shahid — linked to Al Falah University in Faridabad, who are under scrutiny for the car blast near Red Fort, Delhi
- According to the article, Dr Umar was the one driving the car that exploded.
- Investigators say the suspects were in “constant contact” via the encrypted app.
Explanation: This part seems consistent across multiple news outlets (NDTV, PTI etc) and therefore likely reflects the current status of the investigation.

The digital angle of this investigation is what makes the case unique. Instead of mainstream apps, the suspects reportedly used Threema, a Swiss encrypted messaging platform that doesn’t require a phone number or email. In a world full of trackable digital footprints, Threema stands out because it offers anonymity, secrecy and even the ability to operate a private server. Investigators suspect this app was used to share maps, layouts, coded instructions and sensitive planning material. This indicates not only planning but also an attempt to stay completely off India’s cyber radar.
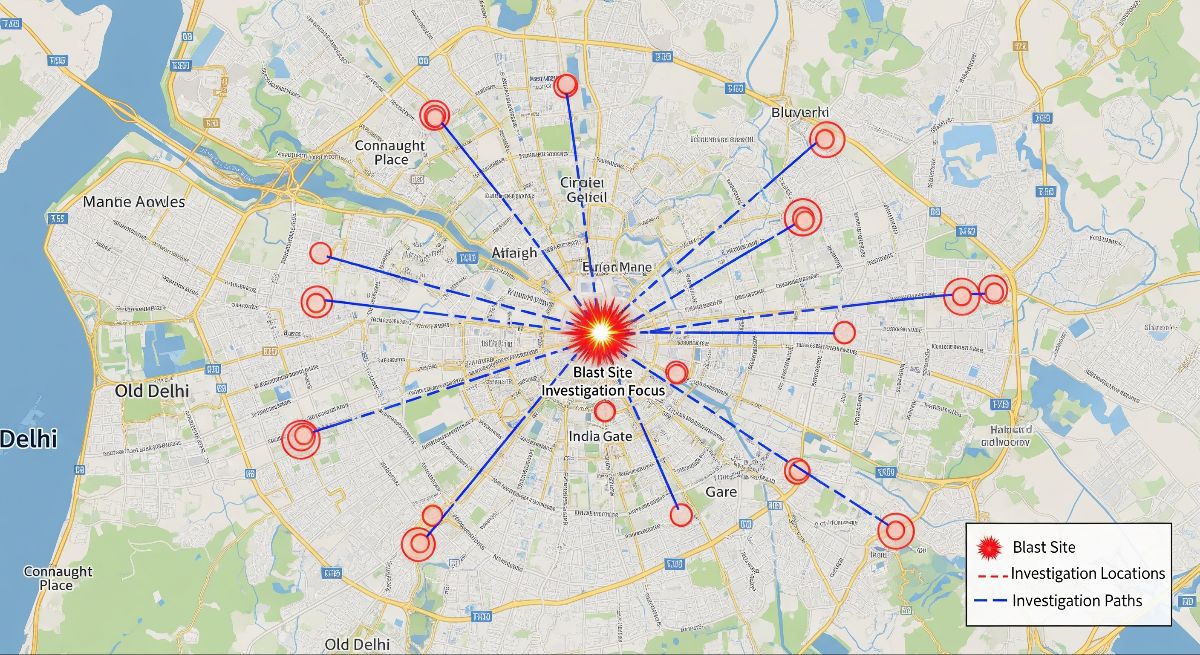
Initial findings reveal that the group conducted multiple reconnaissance visits across Delhi, focusing on historical locations and high-value zones. Shockingly, reports claim that up to 32 cars were being examined or prepared for possible attacks. Whether all these vehicles were actually part of the plan is still under investigation, but the number certainly reflects the scale of the conspiracy.
Use of the encrypted messaging app Threema
Investigators say the group used Threema — a Swiss-based secure messaging app — to coordinate.
- The article highlights that Threema does not require a phone number or email for registration, making tracing difficult.
- It is alleged that a private Threema server was used by the module to share maps, plans and layouts related to the attack.
Explanation: This claim aligns with known properties of the Threema app (end-to-end encryption, optional phone number). It also makes sense in the context of a terror investigation where anonymity would be important. The use of a private server is plausible, and the article states this as an investigative suspicion (“suspected”, “believed”).
Yet, while some facts are clear, others remain in the grey zone. Claims about a 25–30 member network, foreign handlers and private servers are still being confirmed. Investigative teams usually start wide and narrow down over time, so early numbers often change. What is known, however, is that this group operated like a module—a small, connected, secretive unit using technology, intelligence and anonymity to coordinate.
Planning and reconnaissance
- The article says the module carried out multiple reconnaissance (“recce”) in the national capital.
- It also says around 32 cars were reportedly being prepared for blasts near historic and vital installations.
- It mentions the explosion happened outside the Red Fort on Monday evening and the death toll rose to 13 after another injured person died.
Explanation: These points indicate the seriousness of the case and suggest the investigation has uncovered a broader plan rather than an isolated incident. These are credible given the official statements cited.
This case marks a major shift in how terror planning is evolving in India. Earlier, communication was through SIM cards, phone calls, or traceable digital chats. Now the battlefield has moved into fully encrypted, almost untraceable zones. Apps like Threema show how groups can coordinate silently without triggering alarms.
For the public, this case is a reminder: not all terror networks look like what we once imagined. Today they may involve highly educated individuals, using software, encryption and anonymity to plan major strikes. The threat is no longer visible; it hides behind data packets, digital IDs and private servers.
What remains uncertain / needs caution
Extent of the module & network
- While it’s claimed that “25-30 individuals” were involved (source: Deccan Chronicle report) and a “white-coat terror module” spanning doctors, students, etc.
- However, whether all these leads are substantiated, how many have been arrested, or how many were simply persons of interest remains to be confirmed.
Explanation: Investigations often start broad and then get narrowed down; numbers reported in early phases may change significantly. For your version, you can highlight this as a “possible scope” rather than a confirmed list.
Use of a private Threema server
- The article states investigators suspect that “the accused doctors set up a private Threema server to communicate securely …”
- But thus far this remains an allegation/suspicion — not yet publicly proven in every detail.
Explanation: For your audience, it would be wise to mention “according to investigating sources” or “under suspicion” rather than presenting it as a fully verified fact.
 Exactly how the maps/plans were used
Exactly how the maps/plans were used
While the article claims “maps, layouts and restricted documents were shared via the app” and task allocation and location sharing were done through this private network.
But it isn’t clear how far along the planning was (i.e., whether any other attacks had already been set, or whether this was in preliminary stages).
Explanation: Because investigations are ongoing, we cannot definitively say what the full scope of the planning was. It would be prudent to present this in your version as “investigators believe” or “preliminary probe indicates”.
Precise link to handlers and wider geographical spread
- The article hints at “handlers” abroad or overseas, and asks whether the private server was hosted in India or abroad.
- These suggestions are significant but still unconfirmed.
Explanation: For your write-up, you can mention these as ongoing lines of investigation.
Conclusion – Final My Thought
The Delhi blast case isn’t just another headline—it’s a reminder of how modern terrorism is silently shifting from physical hideouts to encrypted digital spaces. Three young doctors, an academic campus, and a Swiss encrypted app like Threema… this combination itself shows how terror networks are becoming smarter, invisible and more tech-driven.
What stands out in this investigation is not just the brutal blast near Red Fort, but the level of planning, the use of private encrypted servers, and the attempt to stay completely off India’s intelligence grid. Yes, many details are still under investigation and some claims remain unverified, but one thing is crystal clear: the threat is evolving.
Going forward, India has to strengthen both its digital surveillance capabilities and cyber-intelligence systems, because the battlefield is no longer just streets and borders—it’s inside phones, apps and encrypted servers scattered across the world.
For common people like us, this case is a warning that the world is changing faster than we think. Terrorism today doesn’t always wear masks or carry guns; sometimes it hides behind degrees, white coats, and high-end tech tools.