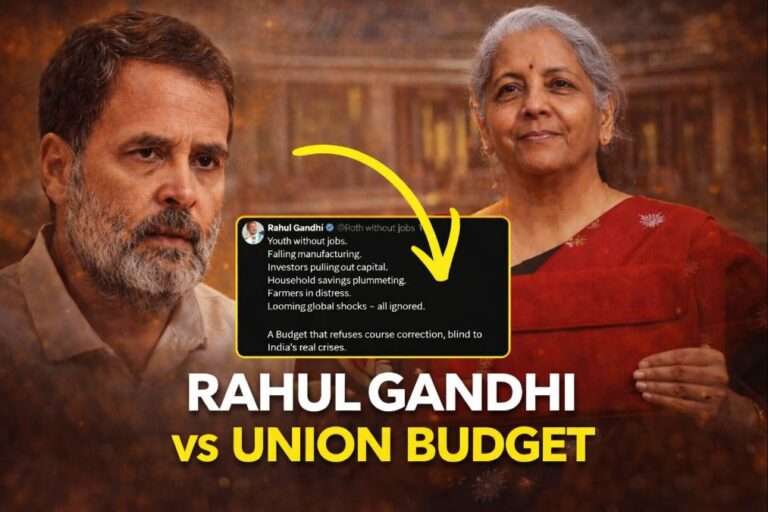
Apple resisted the mandate because forcibly preloading a government app clashes with Apple’s iOS security model, user-consent and privacy commitments, and would create technical and legal risks for the platform and the controversy pushed the government to roll back the mandate.
1) What is Sanchar Saathi
Sanchar Saathi is a Department of Telecommunications (DoT) app/portal intended to help citizens verify device IMEIs, block or locate lost/stolen devices, check SIMs linked to an ID, and report telecom fraud. It’s a government cybersecurity/citizen-service app already available on app stores.

2) What did the Indian government order?
In early December 2025 the DoT issued directions requiring smartphone makers to ensure the Sanchar Saathi app is pre-installed, visible and functional at first device setup on new phones sold in India and to push it by update to some in-market devices, with compliance reports expected within 120 days. That directive set off immediate industry and public backlash.
3) Why Apple (specifically) pushed back the technical & product reasons
- iOS is a walled garden Apple tightly controls what runs on devices. Apple’s security model depends on app signing, App Store review, permissions enforced by the OS, and user-initiated app installs. Forcing a third-party system app (especially one that’s preloaded and enabled at setup) would require Apple to make exceptions to those controls or alter iOS behavior something Apple resists because it can weaken system integrity.
- Preloading vs. pre-approval: app behavior must be auditable on iOS.
Apple typically requires apps to follow its platform rules (sandboxing, no hidden background telemetry, no unauthorized system access). A government app that needs deeper integration with IMEI/telecom backends or device setup screens may need elevated privileges or special APIs and granting those for one country creates precedent and technical complexity. - User consent and default enabled state.
The DoT instructions reportedly wanted the app visible and usable during initial setup, and concerns were raised about whether users could remove it or whether it could be made non-removable. Apple’s user-consent philosophy centers on letting users choose what runs on their phones; preinstalling and locking a government app conflicts with that principle and could erode user trust. - Privacy and surveillance risk perceptions.
Even if the app’s purpose is cybersecurity, critics feared that mandatory preloading and privileged access to device identifiers (IMEI/CEIR linkage) could create surveillance vectors or increase the chance of data collection beyond user expectations. Apple must weigh reputational damage and legal exposure if a device shipped with a government app is later tied to privacy misuse. - Security surface and supply-chain concerns.
Adding preinstalled software expands the attack surface. Apple has historically been cautious about third-party low-level software on iPhones because it complicates patching, creates integration bugs, and can weaken the security guarantees Apple markets to users. That’s a technical reason to push back.

4) Legal & policy reasons (why it’s problematic for Apple)
- Platform policy conflict: Apple’s App Store and device policies don’t support unilateral preinstallation of third-party apps with elevated capabilities. A forced exception undermines platform governance.
- User privacy laws & global precedent: Granting one government a mechanism to push apps onto devices could be cited by other governments with weaker privacy safeguards Apple must consider global legal and PR fallout.
- Contractual and antitrust optics: Forcing preloads touches competition law and user-choice debates; Apple must be careful about how compliance might be characterized legally or politically. (High-level inference grounded in usual legal risk calculus.)
5) Market & business reasons (India-specific considerations)
- Market share vs. principle: Apple’s iPhone share in India is smaller than many Android vendors, so it could be tempted to accept local rules to avoid disruption. But Apple chose product and privacy principles over short-term market convenience because the long-term brand value of privacy matters to its customers worldwide.
- Precedent costs: If Apple accepts one mandated preload, other governments could demand similar special treatment a cost that may outweigh gains from compliance in any single market.
Read This Article Also : Fastest Growing Economies in 2026: India Leads Global Growth
6) What the industry & government reaction looked like
Several handset makers and platform owners (Apple, Google, Samsung, others) expressed unease Apple explicitly told sources it would not comply and would raise concerns with New Delhi. That public and private backlash, together with political criticism and civil society worries about surveillance and consent, led the government to withdraw or revise the mandatory aspects of the directive within days.

7) Technical alternatives that would avoid conflict (practical steps)
(If the goal is device safety and wide reach, here are conflict-free paths the government or vendors could take.)
- Voluntary but prominent installation: Make Sanchar Saathi strongly suggested during setup with clear user choice and an explainer screen (not forced or undeletable). This preserves user agency.
- App-store distribution + OEM partnership: Work with Google/Apple to feature the app in curated setup screens without preinstalling it; offer incentives to OEMs to ship it but keep user removability.
- Open auditing & independent privacy guarantees: Publish source/behavioural audits, third-party code review, and clear data-minimization rules so platform owners and privacy groups can verify no overreach. This builds trust.
- API model with limited privileges: If certain device checks are needed (IMEI/CEIR lookups), expose secure APIs that apps can call without requiring privileged device software. That reduces risk to platform integrity. (Technical best practice.)
8) Broader implications & lessons
- Platforms vs. sovereignty: Governments can set rules for consumer products sold in their markets, but platform architectures and privacy commitments shape what’s feasible.
- Trust matters: Even well-intentioned public-safety tools must be implemented with transparent safeguards otherwise they backfire politically.
Design choices: The way a public digital service is rolled out (voluntary vs forced, removable vs locked) matters as much as the service itself.

Content Originality Statement:
All articles, explanations, analyses, and insights published on this website are entirely original and created through my own research, understanding, and writing. No content is copied, reproduced, or taken from any external source. Every post is written in a clear, human, and meaningful way to provide accurate, valuable information for readers. If external references or data are used, they are properly interpreted and rewritten in my own words. This platform is committed to maintaining authenticity, originality, and high-quality educational content at all times.
Conclusion :
The fight wasn’t about whether Sanchar Saathi can help citizens it’s about how you get that help onto phones without breaking the platform rules, user trust, or device security. Preloading a government app would force Apple to violate fundamental iOS principles (sandboxing, consent, and minimal trusted code), increase privacy and legal risks, and set a precedent that could harm users and the company in the long run. For these reasons, Apple objected. The row shows that tech policy needs careful engineering + open audits + respect for user choice do that, and adoption follows; force it, and everyone digs in.
Read This Article Also : Best Deals & Price Drop Alerts Price History Tracker App